Description
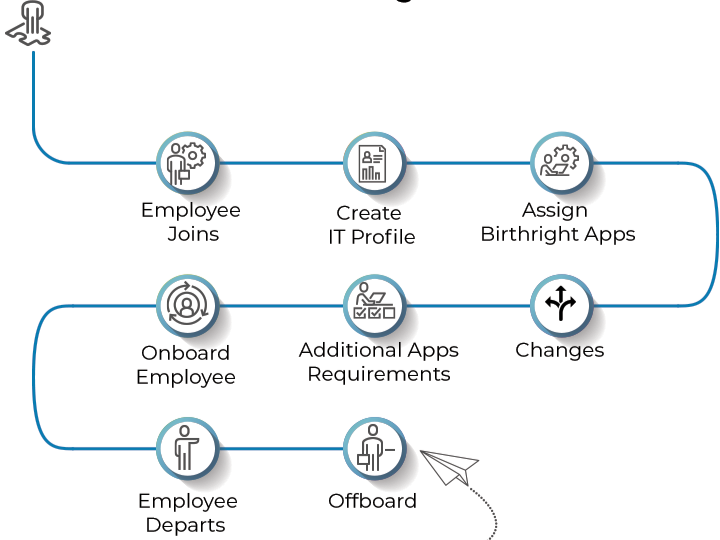
Access Control Lists (ACLs) define permissions and specify who can access or modify resources in a network or system. Misconfigured ACLs often result in either too much access (e.g., unauthorized users gaining access to sensitive data) or too little access (e.g., authorized users being unable to access necessary resources). ACL issues arise from errors in rule setup, poor documentation of policies, or outdated configurations. To avoid these issues, organizations should clearly define access requirements for each user group and use automated tools to review and manage ACL configurations. Regular audits of ACLs can ensure that only authorized users are granted access to sensitive resources. Additionally, it’s essential to implement version control for ACL changes and maintain an audit trail to detect and correct errors promptly. As a best practice, businesses should use more sophisticated role-based models or attribute-based access controls (ABAC) where possible to simplify ACL management and improve security.





Kalu –
“This troubleshooting guide has been an invaluable resource in resolving our ACL issues. The clear instructions and detailed examples made it easy to identify and correct the configuration errors that were hindering access to our protected resources. Thanks to this guide, we’ve restored proper access control and protected our systems from unauthorized access.”
Aina –
“This troubleshooting guide for ACL issues is a lifesaver! Its clear instructions and comprehensive troubleshooting steps helped me quickly identify and resolve ACL misconfigurations, ensuring the security and accessibility of our restricted resources. The guide is well-written and easy to follow, enabling me to solve the problem independently without external assistance.”
Nana –
“This troubleshooting guide was incredibly helpful in resolving ACL issues. The clear and concise instructions made it easy to identify and fix the problem, even though I had no prior experience with ACLs. It saved me a significant amount of time and frustration. I highly recommend this guide to anyone experiencing ACL issues.”
Olusegun –
“This comprehensive Troubleshooting Guide for Access Control List (ACL) Issues has proven invaluable in resolving authorization problems. Its clear explanations and step-by-step instructions helped me identify and rectify misconfigured ACLs, ensuring that sensitive data remained protected while appropriate access was granted. The guide’s effectiveness allowed me to quickly restore system integrity and prevent security breaches.”
Sunday –
“This troubleshooting guide provided invaluable guidance in resolving our access control list (ACL) issues. The clear explanations and step-by-step instructions enabled us to identify and correct misconfigurations that restricted access for authorized users and opened unauthorized access. We were able to implement effective ACLs, ensuring that our resources are protected and accessed by the right individuals. This guide saved us time and effort, allowing us to maintain a secure and controlled environment.”